 Jeremy Boerger
Jeremy Boerger Combat rising IT security costs with IT Asset Management
Pity the poor Chief Information Security Officer (CISO). On one hand, their needs are real: emergent cybersecurity threats are increasingly sophisticated and numerous. On the other hand, the cost of defending against these threats follows the same trajectory. Every organization’s resources are finite, but not investing in the right technology or tactics could place the organization in the same inauspicious gallery as Hollywood Presbyterian[1], Riviera Beach[2], or Colonial Pipeline[3]. Then again, what other value-add IT services should be cut? There is one group inside the department that is in a position to help: IT Asset Management (ITAM). Few CISO and cybersecurity professionals realize the “hand in glove” relationship ITSec and ITAM should have.
In 2016, an article published in a technology research magazine insisted up to thirty percent (30%) of a corporation’s software budget could be cut by implementing a software asset management (SAM) program[4]. The article identifies three best practice activities that must be performed to achieve this remarkable return:
- Optimize Software Configurations — make sure to use the features and tools you pay for, and avoid paying for features and tools you do not use
- Recycle Software Licenses — remove unneeded software installations so the corresponding software license can be applied somewhere else
- Use SAM tools — invest in specialty license management systems that can accurately calculate complex software license rules and point out cost-saving opportunities
In many organizations, software-related expenditures make up a significant portion of the overall IT budget. Any reduction in that line item would fund a number of other projects, so IT Security needs to present a good case to justify redirecting some of those funds to them. Interdepartmental budget strategy sessions can be cutthroat, but most will respect the “Little Red Hen” rule: you only get the bread if you help with the baking. If our intrepid CISO is going to ask for a part of the savings ITAM can deliver, they need to demonstrate how their team, tools, or data are actively helping in those three SAM practices.
Most ITSec professionals are familiar with the ISO/IEC 27000 standards, which require an “asset inventory” to be made of the corporate computing environment. The trouble is, the methodology of ISO 27000 focuses on information security management and does not provide the necessary details and data attributes for effective SAM. But, dig deeper into the supporting standards and you will find ISO/IEC 19770[5], which specifically addresses ITAM and SAM process requirements. Last updated in 2017, it contains a maturity model constructed of three tiers:
- Tier 1: Trustworthy Data — knowing what you have so that you can manage it
- Tier 2: Life Cycle Integration — achieving greater efficiency and cost-effectiveness throughout the asset life cycle (i.e., purchasing, inventorying, using, recovering, and disposing of)
- Tier 3: Optimization — achieving greater efficiency and cost-effectiveness across functional management areas
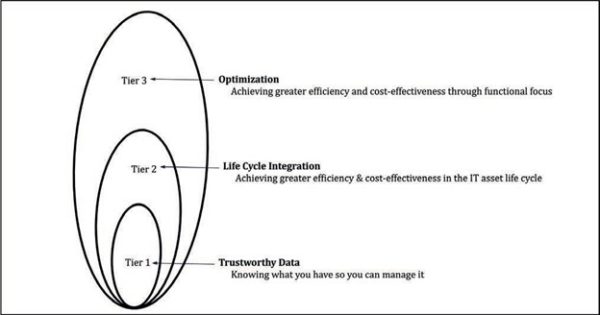
Fig.1 — ITAM Tiers
In typical fashion, the ISO/IEC standards do not describe how “trustworthy data” is obtained or derived, but do describe four processes where ITAM will find “trustworthy data”:
- Change Management
- Data Management
- License Management, and
- Security Management
This makes sense; if IT Security is maintaining an asset inventory (as mandated by ISO 27000), why not harvest reliant parts of their data to build out an asset inventory for a SAM tool just like the one prescribed in the aforementioned Gartner article?
Is that enough, though, for a typical CISO to claim a portion of the ITAM savings for their own expenditures? Maybe not, but let’s consider the second cost-saving source from the Gartner article: recycling software licenses. Typical security vulnerability tools are licensed by either the software agents deployed and installed on objects discovered within the computing environment or by total found objects discovered in a passive sweep of IP address ranges. Unfortunately, IT Security might not catch and remove retired, duplicated, or incorrect records from its own asset inventory lists. That, in turn, risks an over-count of needed licenses and an over-charge to IT Security’s budget. However, if IT Security partners with ITAM and purges recovered and disposed asset inventory records from its vulnerability tools, the overall total cost of ownership for IT Security’s tooling can be significantly reduced. And those savings will unarguably return to IT Security.
The final factor — optimizing software configurations — might seem like a stretch, but IT Security does have a say in the matter. Consider this example: while advising a client a few years ago, the IT Security department identified a number of high-risk security vulnerabilities in the corporate-standard PDF viewer. The CISO recommended removing the standard-issued software outright before the next phishing attack successfully exploited the known bugs within the tool. The IT Service Support team resisted, arguing re-platforming to the IT Security recommendation would be too costly and could be rejected by the end-user community. The ITAM team stepped in, and identified a comparable tool with more features than currently offered (satisfying the end-users), with a better vulnerability score (satisfying IT Security’s concerns), and at a total-cost-of-ownership of 60% less than the current PDF standard (more than covering the cost of deploying the new tool). The moral of the story: simply by engaging ITAM, the CISO was able to improve the security position of his organization without incurring any extra cost to his department or the rest of the organization.
Modern IT Security initiatives are necessary and expensive. Smart CISOs should always be on the lookout for cost-reduction and spend-justification opportunities. Both best business practice proponents and independent researchers identify the IT Asset Management team as a willing partner. By working together, ITAM and ITSec can improve the overall organization’s security position and simultaneously reduce the overall cost of ownership for IT.
About the Author:
Jeremy L. Boerger, the ITAM Coach, founded BOERGER CONSULTING with the idea of helping organizations “cut their software budget without buying less software”. He also speaks professionally to pass along his 20+ years of experience to the next generation of ITAM and SAM professionals. His book, “Rethinking Information Technology Asset Management,” is in paperback and ebooks. He makes his home in Cincinnati, Ohio, with his wife and three children. For more information, please visit www.boergerconsulting.com.
[1] “Hollywood hospital pays $17,000 in bitcoin to hackers; FBI investigating”, Feb. 18, 2016, Los Angeles Times
[2] “How Riviera Beach left the door wide open for hackers”, Jun e 21, 2019, Palm Beach Post
[3] “Cybersecurity Attack Shuts Down a Top U.S. Gasoline Pipeline”, May 8, 2021, NPR
[4] “Cut Software Spending Safely With SAM”, Mar 16, 2016, Gartner ID: G00301780
[5] International Standard ISO/IEC 19770 — Information technology, asset management, Third edition 2017-12









